 A cyber attack on three of South Korea’s major broadcasters and several of its major banks appears to have been caused by a relatively unsophisticated piece of software, security researchers said Wednesday. [Story updated, see below]
A cyber attack on three of South Korea’s major broadcasters and several of its major banks appears to have been caused by a relatively unsophisticated piece of software, security researchers said Wednesday. [Story updated, see below]
The attacks, which began at around 2pm local time on Wednesday (5:00 UTC) left desktop and laptop computers unable to start at KBS, MBC and YTN and took the auto-teller machines at Shinhan Bank and Nonghyup Bank offline. It didn’t affect the ability of the TV stations to put out programming.
The root of the attack was a malicious piece of software identified by computer security company Sophos Labs as “Mal/EncPk-ACE.” The rather forgettable name has resulted in it being dubbed “DarkSeoul” by researchers at the company who analyzed the code on Wednesday.
“What’s curious is that the malware is not particularly sophisticated. Sophos products have been able to detect the malware for nearly a year, and the various commands embedded in the malicious code have not been obfuscated,” the company said in a blog posting.
For that reason — and based on its analysis of the software code alone — Sophos said it’s difficult to conclude the malicious software constituted a “cyberwarfare” attack from North Korea.
Whatever the source, the software was directed at South Korean computers because it attempts to disable two popular local anti-virus scanners, AhnLab and Hauri AV, Sophos said.
 When a computer is infected, the software appears to create several files in the “temp” folder of the PC, AhnLab said in a blog posting. The new files include a routine to destroy the master boot record of the disk — the hard disk’s electronic directory of where information is stored.
When a computer is infected, the software appears to create several files in the “temp” folder of the PC, AhnLab said in a blog posting. The new files include a routine to destroy the master boot record of the disk — the hard disk’s electronic directory of where information is stored.
A computer with a damaged master boot record won’t start — exactly the behavior reported by companies hit by the attack.
In some cases, the malicous code will attempt to overwrite data on the hard disk. In some cases, data is overwritten with the word “PRINCPES” while other cases saw the words “HASTATI” and “NCPES” used, said researchers.
Versions were detected that attack Windows XP, Windows 7 and several lesser used operating systems including Linux, HP Unix, Solaris and AIX Unix.
Separately from the malicious software, network analysis company Renesys said it detected an impact in several South Korean networks as a result of the attack.
 “We observed 5 routed networks of Korea Broadcasting System go down at 05:54:18 UTC this morning (20 March). At the time of this writing they are still down. The Yonhap News Network (YTN) also experienced outages of two of its networks today at 05:54:30 UTC and 06:29:26 UTC.”
“We observed 5 routed networks of Korea Broadcasting System go down at 05:54:18 UTC this morning (20 March). At the time of this writing they are still down. The Yonhap News Network (YTN) also experienced outages of two of its networks today at 05:54:30 UTC and 06:29:26 UTC.”
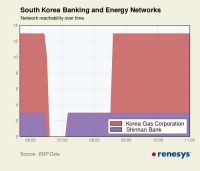
Renesys said it also noticed network problems at Korea Gas Corp., which saw its networks go completely offline for two hours from 15:26:30 local time (6:26:30 UTC). Three networks at Shinhan Bank also went offline at the same time.
The problems at Korea Gas could be coincidental, but Renesys notes that South Korea’s 15,000 networks are usually pretty reliable with only 40 or 50 offline at anyone time, usually for technical reasons.
“However, networks from these sectors (Media, Energy, and Banking) are typically some of the most stable, and the timing of their simultaneous outages seems suspicious.”
03/22 UPDATE: Korea Gas contacted Renesys to tell it the network was deliberately taken offline when the attacks were reported to protect its system.
The attack came less than a week after North Korea’s considerably smaller Internet was hit was an unknown glitch that resulted in difficulty accessing web sites for almost two days. North Korea blamed the U.S. and its allies for a cyber attack but offered no other details of the incident, which was only reported in the country’s foreign media output.
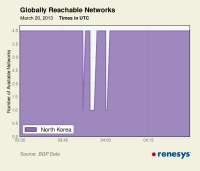 Renesys said it is still observing connectivity issues in North Korea.
Renesys said it is still observing connectivity issues in North Korea.
“Since last week’s disruption in connectivity in North Korea, we have observed additional brief routing outages for the four routed networks of North Korea. On Monday (18 March) and this morning (20 March), we observed outages lasting for just a few minutes in North Korea. It should be noted that although North Korea’s Internet is small, it is very stable. Until last week, North Korean outages had been very rare.”
Additionally, an attack on the website of Internet provider LG Uplus is looking increasingly like it was unrelated to the troubles at the TV stations and banks. The attack resulted in replacing the service’s home page with a page that claimed responsibility in the name of “Team Whois.”
The same behavior wasn’t reported in the other attacks and Sophos said it had been unable to replicate it.




The article mentioned “KBS, MBC and YTN and took the auto-teller machines at Shinhan Bank and Nonghyup Bank offline. It didn’t affect the ability of the TV stations to put out programming.” I was wondering about the effect the disruption was having to the normal broadcasting routine. once I learned of the attack I started watching YTN on Intelsat 19 and the rolling coverage was pretty simple, two anchors and one expert guest and an occasional video piece running in the background. To be honest I’m not sure if the less than dynamic coverage was due to a fair proportion of their resources being offline or the rolling coverage was just a bit dull.
Mark,
I hoped onto KBS World, which was relaying KBS-1 News, and the presentation too seemed pretty basic. Just talking heads in a studio and the same b-roll repeated again and again. But I’ve never found KBS coverage to be “eyewitness news” style.
I think I read somewhere that it did hit some machines involved in production, but obviously nothing central in the broadcast chain.
Martyn