Microsoft has taken control of 50 Internet domain names used by hackers to trick people into divulging their user names and passwords and to plant malware on their machines. The hackers are suspected of being linked to North Korean groups, the company said on Monday.
It grabbed domain names such as “office365-us[.]org” and “pw-change[.]com” as part of a U.S. civil court suit brought against the group, which Microsoft called “Thallium.”
“Thallium specializes in targeting, penetration and stealing sensitive information from high-value computer networks connected to the Internet. The precise identities and locations of those behind the activity are generally unknown but have been linked by many in the security community to North Korean hacking group or groups,” it said in a filing with the U.S. District Court for the Eastern District of Virginia. The case was filed on December 18 but was not unsealed until today.
According to Microsoft, Thallium conducts spear-phishing attacks on groups attempting to trick employees into entering their username and password into a fake website.
“Thallium has targeted government employees, organizations and individuals that work on nuclear proliferation issues, think tanks, university staff members, members of organizations that attempt to maintain world peace, human rights organizations, as well as many other organizations and individuals.” — Microsoft court complaint
The emails are either crafted to appear to come from a friend or contact, or from a service provider explaining a problem with an account or that suspicious activity was detected.
The objective is the same: to direct the user to a website that is controlled by the hackers but dressed up to look like the official one.
The hackers chose domain names that looked legitimate, or would pass as legitimate without close scrutiny. In several cases, this involved registering domain names where an “r” and “n” take the place of the letter “m.”
Examples include “hotrnall[.]com,” intended to look like “hotmail.com,” and “hanrnaii[.]net,” intended to look like South Korea email service hanmail.net.
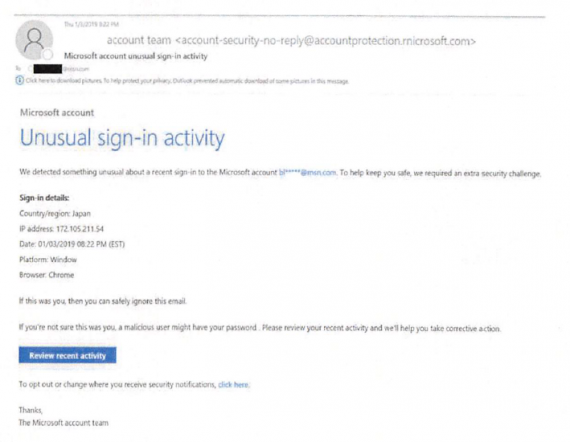
A spear-phishing email sent from Thallium (Photo: Microsoft)
If the attack is successful, Thallium hackers use the stolen credentials to regularly log into the account and check for emails, contacts or calendar entries of interest, the complaint said. On many occasions, the hackers also create a new mailbox rule to forward new emails to a Thallium-controlled account. By doing this, the hackers can retain emails even after the target deletes them and will continue to receive new emails even if the password to the email account is changed.
In addition to spear-phishing emails, the group also planted malicious software on the computers of some targets. The group used similar look-a-like domain names to trick users into installing the malware, which was designed to steal data off their machines.

